SSHLock
A safer and powerful alternative to traditional password-based access mechanisms.
SSHLock is a software security product that implements the innovative security concept described in : SSHLock: a secure access mechanism - A white paper, by Franck Porcher, PhD.
SSHLock mimics the key features found in real security access locks (eg. bank entries) to provide IT systems with a super-secure access mechanism called an "sshlock".
An sshlock is essentially a restricted pass-thru device between the outside world and the computer's content -two environments that should not be in direct contact with one another. It is secured at both ends by tight monitor and control access mechanisms, just like bank's security doors, designed to screen access requests and make unauthorized entries impossible.
SSHLock brings's a wealth of security features that turn your computers into impenetrable bastion hosts, providing a safe, easy and reliable access for authorized people while transparently defeating attackers' attempts to break in.
SSHLock is a powerful and desirable alternative to the vulnerable traditional password-based access mechanisms.
SSHLock is not a repair kit aimed at fixing a compromised computer.
SSHLock is a preventive security product specifically designed to ensure your are not becoming the next cybercrime statistic, either as an individual or as a sysadmin in charge of your company's valuable IT systems.
Password attacks are the simplest and the most common means to break in IT systems. Unless we ourselves become a cybercrime victim, we may never know just how much of a problem malicious hacking is :
The main causes for this situation are the vulnerabilities that plague the traditional password-based authentication mechanism that still is today, by far, the most common way to access a computer :
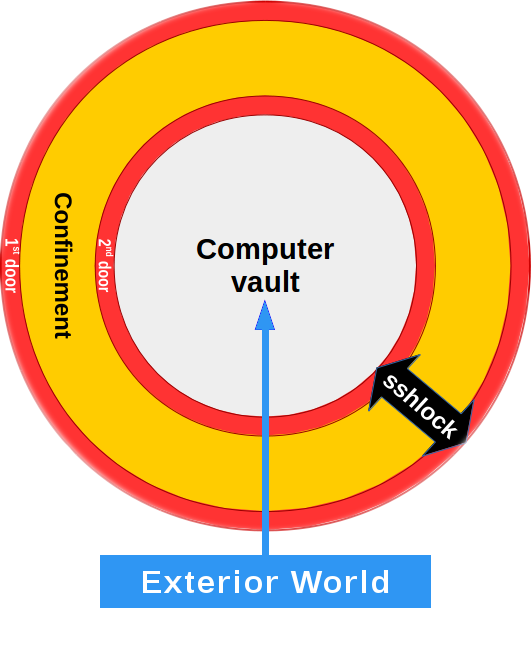
An "sshlock" (cf. diagram on the right) is essentially a restricted pass-thru device (i.e. a "buffer") between the outside world and the computer's content -two environments that should not be in direct contact with one another.
The "sshlock" (cf. diagram on the right) is secured at both ends by tight monitor and control access mechanisms designed to screen access requests and make unauthorized entries impossible (just like a bank's security doors).
The following are obvious scenarios where using SSHLock shines:
Available for
![]()
![]()
![]()
![]()
![]()
![]()
Its secure layered access architecture (see diagram on the left) is designed to remove all threats associated with password security attacks, making any attempt to break in your machines and steal your valuable content virtually impossible.
SSHLock
brings the following security benefits out-of-the
box :
However, this extra security does not have to come at a cost.
SSHLock seamlessly integrates with your computing
platform :
We are working hard towards completing a live, online sandbox where you could play your mind installing and running SSHLock. However they are a few challenges on the path -- security and scalability for instance -- and it might just take us a little while more before this is completed.
In the midtime, there are a few acceptable substitutes:
Available for
![]()
![]()
![]()
![]()
![]()
![]()
1. Download the SSHLock tarball
Pick-up the tarball that closely corresponds to your hardware
platform (e.g. i386, x86_64) and your Operating System.
For example : sshlock-1.26-freebsd-x86_64-20161218-024039.tar.gz
2. Extract the SSHLock tarball
3. Check the integrity of the SSHLock software
4. Install the SSHLock software
1. Review the SSHLock usage
$ cd ~
$ sshlock -h
2. SSHLock' your machine
$ cd ~
$ sudo sshlock -C \
-N "public.DNS.name.of.this.machine" \
[-p custom-port] \
[-u custom-sshlock-accountname] \
[-w custom-cmdproxy-name]
3. Install your cryptographic keys to allow SSHLock to grant you access
$ sudo sshlock \
-i $my_identity \
-K $my_ED25519_public_key_file \
-k local-account \
-P $passphrase
4. Install your SSHLock Product License(s)
To buy your SSHLock Product License, please see "License" below.
Once your transaction is completed, you will receive an email to invite you to proceed with installing the SSHLock Product Licenses you just bought on your machines (SSHLock licenses never expire. You need one license per machine to protect).
We have worked hard to make the process of installing SSHLock Product Licenses as simple and transparent as possible. The email you will receive will include a master-code. To install an SSHLock license on a machine, given you already have installed the SSHLock software, simply start SSHLock on the machine and provide the email address that was used for buying the licenses as well as the master-code as shown below (the "," between the email address and the master-code is mandatory):
$ sudo sshlock -S -L "email@address,master-code"
To review the SSHLock Product License on a given machine, simply run the following command:
$ sudo sshlock -S -P
Please let us know of any concern you may have, or any difficulty you may experience in installing and using SSHLock. We can help you in several different ways!
Enable SSHLock to start automatically
$ sudo sshlock -I
Harden SSHLock (if you are paranoid as I am)
$ sudo sshlock -H
Uninstalling SSHLock
$ sudo sshlock-installer -u
As a young and independant software engineering company specialized in releasing high quality innovative software products, the product licenses you buy from us are our only source of income to recoup our investment and to keep going with what we love to do best.
The price of our software products is set reasonably low so anyone genuinely interested can afford it. You need a single SSHLock Product License per machine you want to protect with SSHLock. SSHLock licenses never expire, and can easily be transfered from a machine to another, or reinstated upon a platform software reinstallation.
Our general policy is to turn all our products into Open-Source software once we have recouped our initial investment (plus a little bonus to help us fund our next products). To remain absolutely independant, we refuse any kind of sponsorship : as individuals and corporate IT sysadmins, you are our only sponsors!
Some companies fund their work by maintaining two versions of their products, usually a full-featured commercial version and a free downgraded Open-Source version. We dislike the ethics behind the idea : not only does this cost more resources to produce and maintain without any added value (someone has to pay for this extra work somehow, usually you ;) ), but we believe it also fuels the "caste war", something we oppose.
When SSHLock becomes open source, hopefully in a year or two, maybe sooner, everyone will have free access to the full-version at no cost.
I am convinced. Please take me where I can buy a SSHLock Product License.
Terms of Use
The "Terms of Use" pertaining to the use of the SSHLock software product are consigned in the file "LICENSE" that comes bundled with the software. Though we have kept it simple and really short (no salmigondis here), we still recommend you spend a few minutes to read it.
Paying with PayPal is secure and fast. PayPal is the number one, most secure and most renowned solution for securely buying on line.
Buying with PayPal is easy : you buy online from millions of websites from 200+ countries all around the globe, using your choice of PayPal payment at checkout : your bank account, your credit card, your Visa Debit card, or your PayPal balance.
Paying with PayPal is secure : you log in to shop online with just your email and password. You can forget entering all your credit card numbers and leave these precious credentials behind you. PayPal never shares your financial information with merchants.
Using PayPal is free to you. The seller is the one charged to securely handle your payment.
Shopping with PayPal is safe : PayPal protects your eligible purchases, so if an eligible item doesn’t show up, or turns out to be different than described, we’ll help sort things out with the seller.
Modus Operandi
Pricing
| Number of licenses | Discount | Unit Price (USD) | Bundle Price (USD) |

|
|---|---|---|---|---|
| 1 | 29 USD | 29 USD | Buying this item is momentarily suspended | |
| 3 | 5% | 28 USD | 83 USD | Buying this item is momentarily suspended |
| 5 | 12% | 25 USD | 125 USD | Buying this item is momentarily suspended |
| 10 | 20% | 23 USD | 230 USD | Buying this item is momentarily suspended |
| 50 | 30% | 20 USD | 1000 USD | Buying this item is momentarily suspended |
| >50 | For bulk quantity (more than 50 licenses), you are welcome to contact us directly at: franck.porcher@protonmail.com | |||
Our engineers team is committed to help you with your particular situation, your needs, or with any difficulty you may encounter in installing or using SSHLock.
When it comes to value for money, we believe the best support you will get from us will come from enrolling into our dedicated live, online SSHLock seminars.
However, we are open to consider any form of custom technical support you feel will support you better, for instance -- but not limited to :
Should you prefer to receive a customized support plan to match your agenda, you are most welcome to contact us by email and provide us with a preliminary description of your needs (please refer to our email address in the footer below). We will follow-up with appointment suggestions for a video conference to discuss them further.
A great experience.
As an integral part of our support offer, our live, online seminars are, by far, the best and most casual way to get your hands on SSHLock technology and gain invaluable knowledge and Case-Based experience in learning, setting it up, and using it.
Experience one of the most user-friendly video-conference platform, and engage with our high-tech, easy going IT engineers to master the ins and outs of this innovative security technology from the comfort of your home or your workplace. Save money and time by reducing travel, while retaining the benefits of face-to-face exchange.
You will have the opportunity to try SSHLock in a real situation, to meet technical people from around the world who are sharing the same paramount concern for IT security, and to exchange your valuable knowledge while gaining from others' experience in setting and using SSHLock.
Flexible settings.
Our SSHLock online seminars are two-hours long, and limited to ten persons in order to maximize your experience. All registrants participate in the same video-conference using the device of their choice : a desktop computer, a laptop, a tablet or even a mobile phone. The simplicity of use remains the same regardless of the device, offering unprecedented possibilities concerning interaction and data sharing to all.
Our schedules are never pre-set, but dynamically configured to best arrange everyone's agenda, including out-of business hours, week-ends and holidays.
Quality training.
Most our seminars will be lead by SSHLock's team leader, computer scientist Dr. Franck Porcher, PhD., and author of the SSHLock innovative concept. Dr. Franck Porcher has proudly accumulated thousands of hours of professional training and teaching IT courses in an University's master degree during the last twenty years.
Program
We offer two different seminars to accomodate most needs.
1. Hands-On SSHLock
2. Support and TroubleShooting SSHLock
Pricing.
69 USD per participant, per seminar.
How to register ?
Upon receiving your registration, we will contact you to propose you a range of possible dates to choose from.
Thank you!
Buy a seminar ticket
This section will fill-in as need arise.
Despite our genuine dedication to produce bullet-proof high-quality code, and the necessary time we take to extensively testing it, there is always the possibility of some hidden issues, hopefully minor.
Before reporting a problem, please make sure you have consulted our FAQ and have not found any satisfactory solution to your problem.
To report to us what you believe to be a dysfunctional behavior, please run the following code and send us the resulting file at our email contact below (see footer). We will analyze the situation and get back to you.
$
$ {
$ uname -a;
$ id -u ; id -un;
$ ls -l /etc/sshlock.conf;
$ cat /etc/sshlock.conf;
$ sshlock -V;
$ sudo sshlock -dPslTc
$ } &> "/tmp/sshlock-bugreport-$(date "+%Y%m%d%-H%M%S-%z-%s")"
$